Imagine what it would be like:
It’s a typical day, and you’ve just checked your email.
You see one from a familiar source with a zipped attachment, and you promptly download it.
You unzipped the file, and nothing happens, so you move on to the next email and continue with your mundane routine of opening emails while wondering what exactly happened.
Then all of sudden you find yourself staring at a notification that came out of nowhere.
“Your Computer has been Locked,” it says, and as you read through the rest of the message, you now realize that you have to pay money to get access to your files again.
You try opening your files but to no avail - it has already been locked away using powerful encryption, and the only keys are with cybercriminals asking for your money.
Ok, we know what you are thinking:
Yes, you have just been a victim of a ransomware attack - one of the biggest cybersecurity threats of 2016.
Even if you cannot relate (yet), doing nothing might be setting yourself up to be the next victim with an expected rise of ransomware attacks in 2016.
If you’ve been a victim, you’re not alone as there have been 4 million ransomware samples identified in the 2nd quarter of 2015 with 1.2 million of them being new at the time.
There’s a reason why the ransomware trend continues to grow - it’s just far too effective and people aren’t doing anything about it.
What is Ransomware?
Deriving from the words “ransom” and “malware,” its basic premise is that it takes away access from data and asks for payment to get back this privilege.
Depending on the variant, and there are plenty out there, it will use various tactics to hustle you into paying such as
giving you a payment due date lest your access will forever be revoked or
by spoofing the FBI and scaring you into thinking that your PC has been involved in some illegal activity and is now locked out unless you pay.
The objective is to fool you into paying as soon as possible.
There are two primary forms of ransomware circulating:
(1) Locker Ransomware
Locker Ransomware will deny you total access to your computer’s operating system.
This effectively stops regular operations and only preserves minimal functionality required to make the payment and restore your system.
Most of these are of the older variant of ransomware, and there are some ways to recover from by cutting the malware off your system.
(2) Crypto Ransomware
Crypto Ransomware is a much more advanced variant as it uses encryption to lock your files away in plain sight instead of locking you out of your computer entirely.
Despite having access to the data, it is far more dangerous as encrypted files are virtually unrecoverable without the key bar some very rare exceptions.
It’s stressful as it indiscriminately targets our current lifestyle of being reliant on our computers to keep precious files or critical data while also relying on the internet as our primary source of content consumption.
Malware authors know this and will use every play in the book to get the opportunity to exploit your files for money.
6 Common Types of Ransomware
We have prepared a list below to help you identify the 6 different types of ransomware:
Cryptolocker
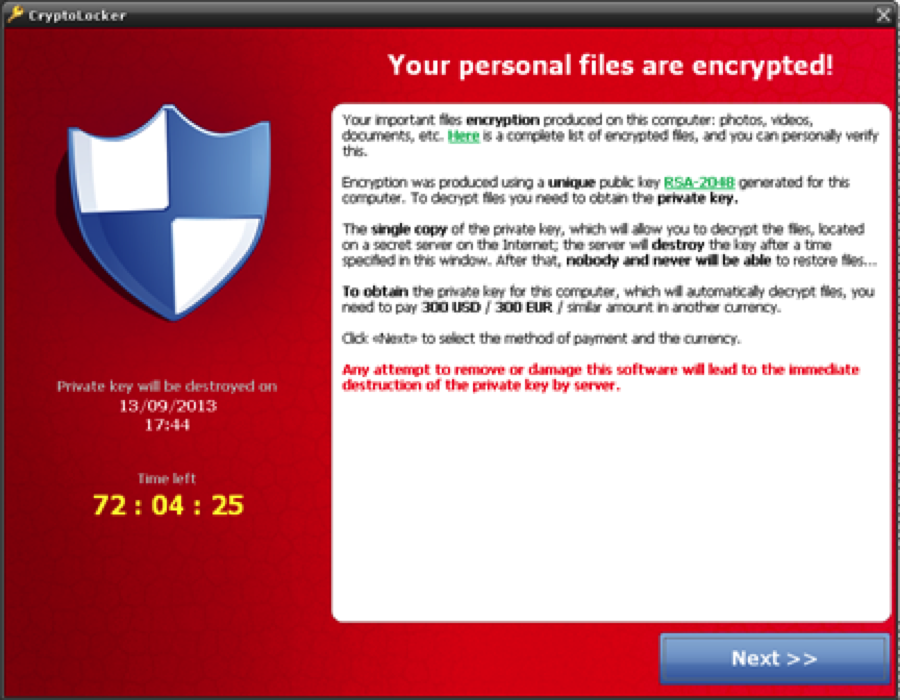
Cryptolocker is spread via infected email attachments or secondary infection on computers with viruses that offer backdoor access for further attacks.
Once your computer is infected, it will encrypt your files stored on local and mounted network drives.
There is no way you can decrypt it by your own means since they store the information needed to decrypt at the malware’s central servers.
The malware will then display a message asking for a payment (either bitcoin or pre-paid cash voucher) to decrypt the files within a stated deadline.
Otherwise, it threatens to destroy the information if the deadline passes.
Cryptowall
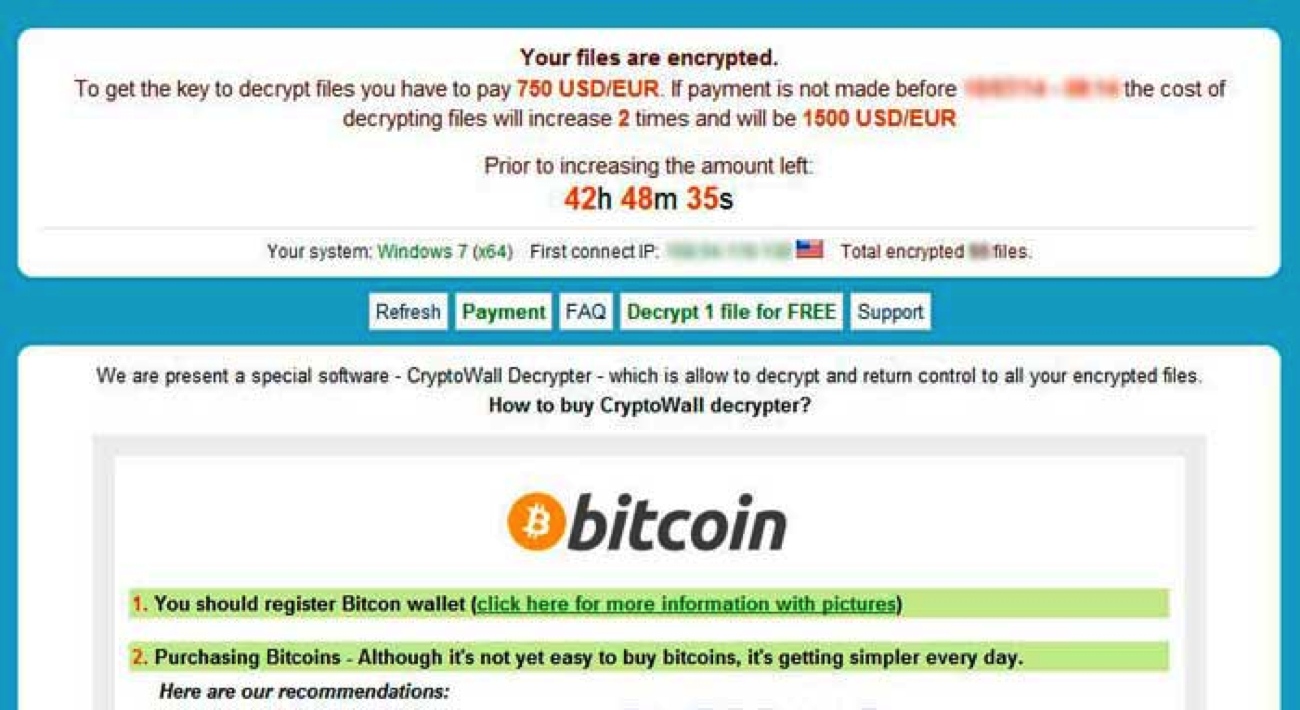
Cryptowall infiltrates your computer’s operating systems through spam, malvertising, infected email messages, fake downloads, and updates.
Once they have successfully infiltrated, it will encrypt specific files and demand a ransom payment in bitcoin to decrypt it.
The amount of ransom may differ depending on your location.
Cryptowall has also appeared with a variety of names such as Cryptorbit, CryptoDefense, CryptoWall 2.0 and CryptoWall 3.0.
The two telltale signs that show Cryptowall infected your computer are
(1) data may not display correctly after successfully launching specific files (e.g., doc, .xls or .pdf) with the correct program, an error message may also pop up and
(2) you will see the following three files at the root of every directory containing encrypted files:
-
-
- HELP_RECOVER_INSTRUCTIONS.PNG
- HELP_RECOVER_INSTRUCTIONS.HTML
- HELP_RECOVER_INSTRUCTIONS.TXT
-
CTB-Locker
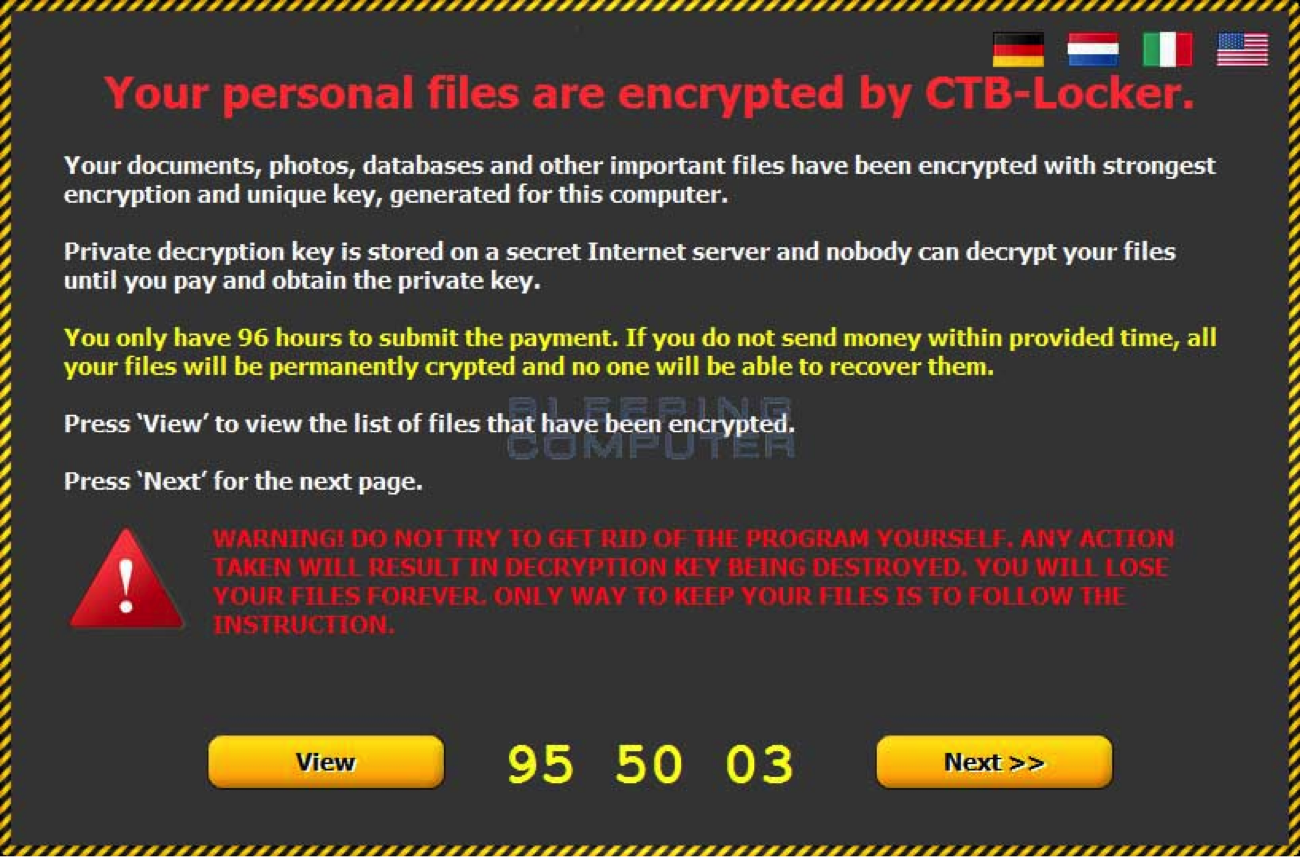
CTB-Locker spread through aggressive spam or misleading email.
The email message claims you have a fax message, purchases or payment approval that require your immediate attention.
Once they have tricked you into downloading the fake zipped attachment and accessing the downloaded zip file, your files will be encrypted, and a ransom payment needs to be made to receive the decryption key.
You should also be wary of those annoying pop-ups offering you to update your programs such as Java or Flash Player while surfing the web page.
This may also lead to CTB-Locker infiltration.
History of CTB-Locker's Name
Here is a little history of how the ransomware name came about. CTB is the acronym for Curve-Tor-Bitcoin.
Curve is for persistent elliptical curve cryptography that encrypts affected files with a unique RSA key.
Tor is for malicious server placed in onion-domain (TOR), that pose a difficult challenge in taking it down.
Finally, Bitcoin is the payment method which avoids tracing back compared to the standard payment systems.
Locky
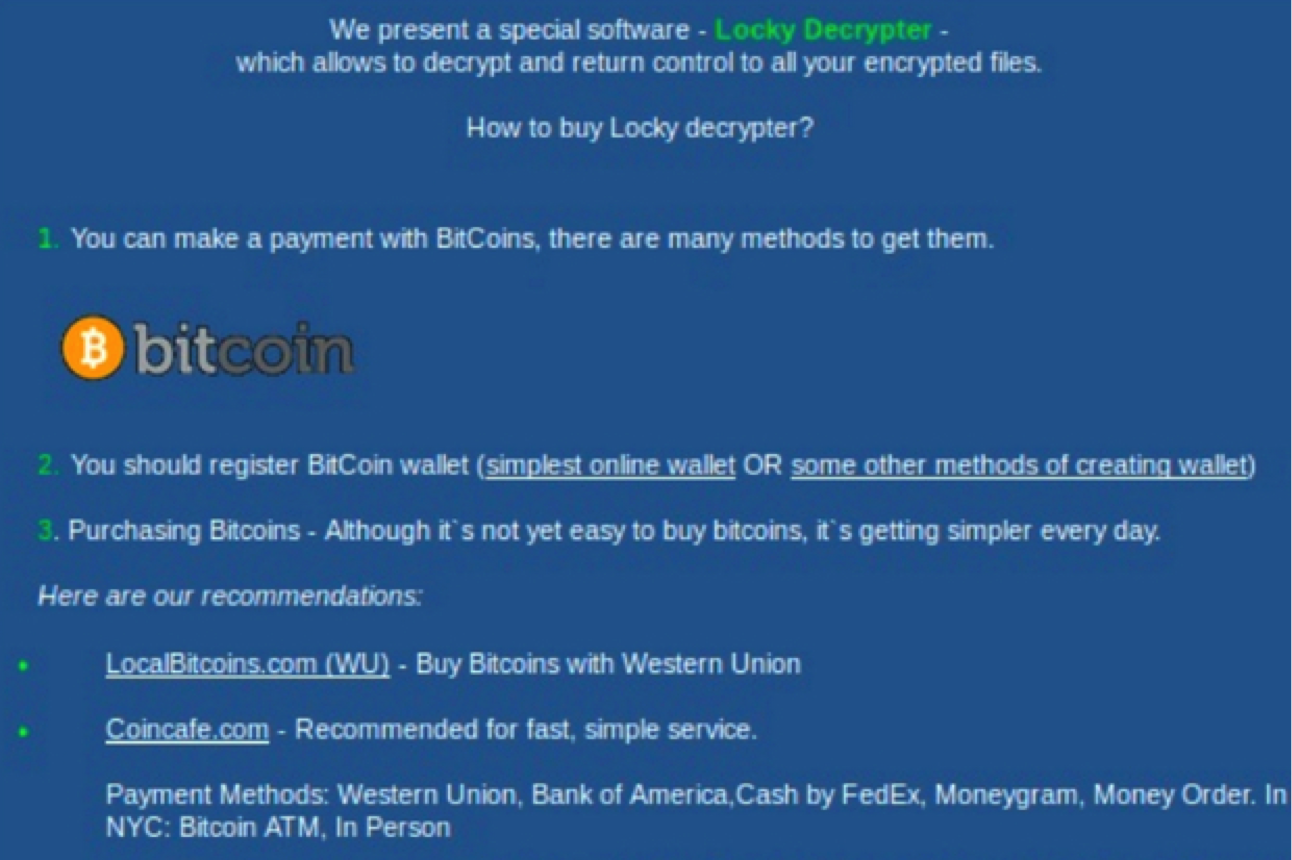
Locky’s approach is familiar and similar to the previous ransomware mentioned.
Malicious files such as .doc, .pdf or .xls attached to spam email messages. is where you can find the hiding place of Locky.
The authenticity of the email message seems real since they try to disguise themselves as an invoice or resume that you receive regularly.
When you open up the file and enable the macros to read it, an executable file aka ransomware is activated and starts to encrypt your file.
Once encrypted, you will need to pay a ransom using Bitcoin.
Teslacrypt
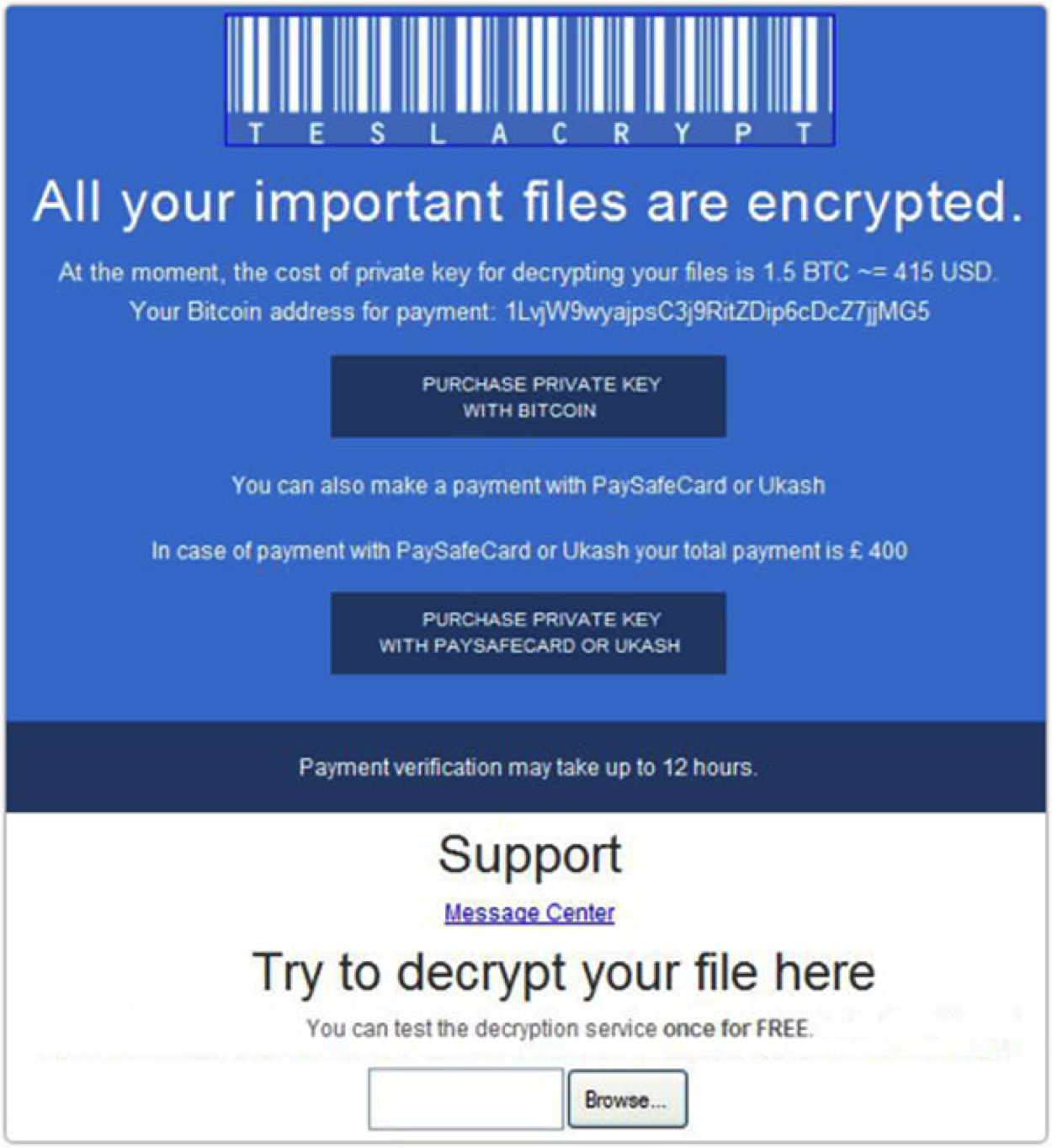
TeslaCrypt is another new type of ransomware that encrypts your files using AES encryption.
It is typically spread via the Angler exploit kit explicitly targeting Adobe vulnerabilities.
It installs itself into the Microsoft temp folder by exploiting the vulnerability available.
Similar to other ransomware, you will have to make a payment (either PayPal My Cash cards or BitCoin) to decrypt your file.
What sets TeslaCrypt apart from the other ransomware is the encryption of video game-related files such as save data, player profiles, custom maps and game mods stored in the hard drive.
Favorite games such as MineCraft, World of Warcraft and Call of Duty are one of the 40 video games targeted by TeslaCrypt.
Fortunately, the TeslaCrypt developers have put an end to this rogue business and released the master decryption key for free in mid-May of 2016.
TorrentLocker
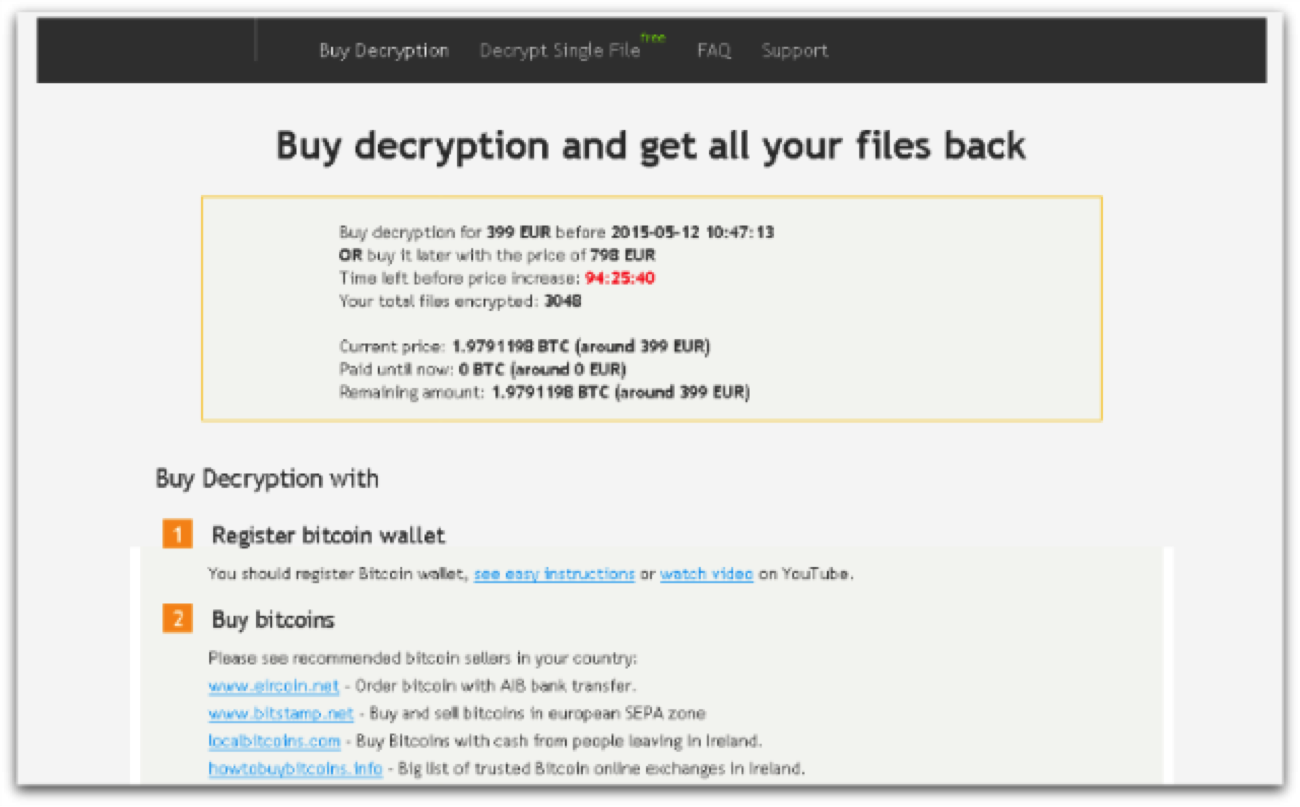
TorrentLocker is usually distributed through spam email campaigns and target geographically by delivering messages to specific regions.
It uses AES to encrypt a wide variety of files and demands a ransom payment in bitcoin after completing the encryption.
The uniqueness of TorrentLocker lies in harvesting the email addresses from your address book to further spread the malware.
It is often referred to as “CryptoLocker” due to the similarity in their names.
How to Protect Against Ransomware
Ransomware attacks have been rampant over the past few months with some grabbing headlines over the news such as the University of Calgary paying a ransom of $20,000, Holly Presbyterian Medical Center paying $17,000 worth of Bitcoins and more.
While no one is willing to fork out a hefty sum to pay for decryption, this is generally done out of desperation when access to the files is crucial or if irreversible consequences are inevitable.
However, the threat of ransomware is not insurmountable.
Here we have five simple tips that will help to protect against ransomware:
1. Awareness and Education
You don’t have to turn yourself into a security expert to understand the technical details of ransomware, but you should educate yourself on the best safety practices and pay attention to the possible threats out there.
Heighten your awareness by reading up on how the latest ransomware work and spread.
2. Backup Your Data Regularly
This is by far the simplest and easiest habit to cultivate.
Remind yourself to backup your files onto an external device that is not connected to the network and remind yourself to unplug it as soon as the backup finishes.
Even if a hacker gets into your network, they would not be able to infect your backup solution and prevent you from accessing it.
You do not have to do it daily (unless you regularly create files that are really so important) but make it a weekly or bi-weekly routine.
Should you be infected with ransomware, you can at least wipe your computer clean and restore to the previous backup.
3. Keep Your Software Updated
Malware authors can exploit outdated software with known vulnerabilities to get onto your system.
Make it a practice to update your software often to decrease your chance of getting attacked by ransomware.
Enable automatic updates if possible or head straight to the software vendor’s website for new updates since malware authors may disguise their ransomware as software update notifications.
4. Be Careful of Email Attachments or Links
This will require some conscientious effort when you are checking your email.
There are evident factual discrepancies that you can spot in the email to protect yourself against ransomware.
For instance, if you receive an email from the bank or your friend claiming that they have received something from you, make it a habit to stop, think and verify this.
These can be spam emails that use social engineering to persuade you to download an attachment or click on a link.
Also, if you receive strangers’ email or reputable companies with foreign email domain, avoid clicking the links or opening attachments.
If you have to click on a suspected link, remember to hover over the URL or hyperlinked text.
This should cause the landing page URL to appear so you could check if you trust that domain.
That being said, if the landing page shown is a URL shortened link (i.e. bit.ly/adrde), try to avoid these at all costs as reputable sources don’t do this and is usually a sign that efforts have been made to hide the landing page URL.
5. Go for Multi-Layer PC Security Protection
Having both anti-virus software and firewall is always a good idea as it helps you to identify threats.
A 2016 report by PandaLabs has found that there are 227,000 new samples of malware created daily and that number will continue to grow in the future.
Majority of these remain undetectable in the first few hours of release, and some will even elude detection for more extended periods.
This means that your current anti-virus’ virus detection may not be as timely and accurate enough to protect your computer.
It is recommended to add on another layer of security for your PC.
More often than not, the ransomware runs secretly and silently encrypt your file without you knowing until you receive the message to make the payment.
PC security solution with application whitelisting can help block suspicious applications that you did not consciously launch.


